To say that the COVID-19 pandemic impacted our lives is an understatement. From social distancing and lockdowns to drastic fluctuations in the workforce that affected millions, the world is still feeling those repercussions as of 2021.
Unfortunately, while the world is slowly recovering, hackers and cybercriminals have been hard at work. As screen time increased and businesses went remote, the window of opportunity for hackers increased. But the pandemic was not an isolated incident of increased cyberattacks.
To date, 30,000 websites are hacked daily and there is a new attack deployed somewhere on the Web every 39 seconds.
IoT devices are experiencing over 100 million attacks worldwide every year. One of the more memorable recent attacks shows just how sophisticated these cybercrimes can be and why skilled cybersecurity professionals are always in high demand.
In this article, we’ll cover the following topics:
- Why is cybersecurity necessary?
- What do cybersecurity professionals do?
- What skills do you need to be a cybersecurity professional?
- Where should you start your cybersecurity career?
- Entry-level cybersecurity jobs
- How much do entry-level cybersecurity jobs pay?
- Major local industries for cyber jobs
Why is Cybersecurity Necessary?
The attack on SolarWinds, an IT infrastructure management software company based in Austin, Texas, began as early as September 2019 and went unnoticed until December 2020. During this time, back doors were inserted into software updates, malicious malware was downloaded and attacks were deployed on select individuals.
This resulted in the company’s clients, including state and local governments as well as federal agencies and courts, becoming affected. Some experts estimate the damage amounted to $100 billion but the real damage is the inability to pinpoint what information was accessed, what communications were read and how this may affect national security for years to come.
You see, cybersecurity is not about stopping mysterious hooded hackers, as movies would have us believe. It’s about protecting our information, individually and nationally, from the slew of threats.
When you choose a career in cybersecurity, you’re choosing to be a defender of the masses against the most elusive and malicious enemies. You’re choosing to make an impact in your communities and help those around you enjoy the internet and their beloved devices with peace of mind.

What Do Cybersecurity Professionals Do?
If you’re wondering what life is like as a cybersecurity professional, you may think it’s mostly spent in a server room or hunched over a laptop all day. While these may reflect some part of your day, the majority of what your day looks like depends on what your role is. Cybersecurity professionals aim to build secure networks and devices, detect and mitigate threats, lead recovery projects and, in general, protect individuals and organizations from costly cyberattacks.
This is a general overview of what cybersecurity professionals do, so to get an idea of where you can go in your tech career, let’s explore the types of cybersecurity in today’s workforce.
Types of Cybersecurity
Network security aims to protect the networking infrastructure of an organization. Multiple layers of defense protect the network from unauthorized access or misuse with specific policies and controls set within each layer. Types of network security include firewalls, VPNs, Access Control, application security and anti-virus software. Network security contains a variety of roles and spills into the other types of cybersecurity types.
Application security keeps the apps on your smart devices secure, despite inherent vulnerabilities. Organizations today are using multiple applications to communicate and share important information. To keep sensitive data from prying eyes, the cybersecurity professional must maintain security policies and procedures, document application security controls and design technical solutions to address potential vulnerabilities.
Endpoint security aims to ensure that IoT devices on a network or in the cloud are secure from cyber threats; this includes desktops, laptops and smartphones. To make sure these devices and their users are staying protected, modern security systems are being designed and implemented by skilled professionals. As connected devices become more prominent in our day-to-day, in the office and in our homes, this type of cybersecurity is a must.

Cloud security is the concept of protecting cloud-based systems, infrastructure and data. Today, cloud storage is one of the most common uses of cloud computing, with hybrid cloud and multi-cloud solutions becoming available in recent years. Cybersecurity professionals involved in cloud security are tasked with keeping up with evolving, sophisticated threats to provide centralized, reliable security at reduced costs.
Just about every type of role in the field meets one or more of these types of cybersecurity. There is no need to decide if you want to “specialize” in one or the other because chances are you will touch each one throughout your career. As long as there are networks and devices, there is bound to be a need for skilled cybersecurity professionals to act as the only defense against online attacks and ransomware.
What Kind of Skills Do You Need to Be a Cybersecurity Professional?
In any industry, there are certain skills every professional must have if they want to go far. When it comes to cybersecurity, these critical skills boil down to being strategists, strong communicators and having the mindset of a life-long learner.
Communication
Whether it’s with your team, clients or stakeholders, every cybersecurity professional must know how to communicate and be an active listener. Part of this is having presentation skills to show others why certain protocols are necessary and how to manage them at an individual level.
Technology is not something that everyone can easily grasp, that’s why knowing how to interact with others outside of your team in meaningful ways is necessary for protecting the systems you’re charged with. Additionally, communication is essential for properly training your team and managing them to excel in their respective roles.
Strategy
It takes a critical mind to understand how to implement security measures, weigh the consequences of any action and understand the mind of a hacker. No matter where you go in your cybersecurity career, approaching your tasks strategically can position you as a reliable leader within your organization and team. Learning ethical hacking and game theory are great ways to hone this skill.
Life-Long Learning
Cyber threats are everywhere and become more sophisticated every day. Hackers and cybercriminals make it necessary for cybersecurity experts to be on the lookout for new developments, meaning they must make time for research, upskilling and reskilling and earning industry-standard certifications. If you’re naturally curious, a career in cybersecurity would suit you well!
Additional Skills
Of course, there is a collection of hard and soft skills that would complement the universal three previously mentioned. The following is not an exhaustive list but can give you an idea of where to get started if you do not already have experience in the field.
Soft skills
- Problem-solving
- Attention to detail
- Collaboration
- Team leadership
- Independence
- Creativity
- Research
Hard skills
- Networking and network attacks
- File system and error handling
- Intrusion Protection Systems (IPS)
- Security Information and Event Management (SIEM)
- Endpoint security
- Python automations for security
- Industrial IoT
Where Should You Start Your Cybersecurity Career?
Many professionals with experience in the field find it easy to pivot to a cybersecurity career since they are familiar with some IT concepts. Having worked as a Help Desk Specialist or software developer gives you an advantage if you decide to pursue a cybersecurity career in the near future.
Having experience, however, is not always necessary for breaking into the field. It is possible to work in an unrelated field and still emerge as a skilled cybersecurity candidate with the help of industry experts and hands-on training.
The Cybersecurity Professional Bootcamp at NJIT is a professionally developed program with the needs of today’s workforce in mind. Train part-time on evenings and weekends with active professionals who take the time out of their work to instruct the next generation of cybersecurity experts. Spend time in simulation labs to work on real-life scenarios you will face in the field and work with career services to develop and polish your resume, establish your online presence and practice interview skills. Reach out to our admissions team to learn more or click below to download our course catalog and see what’s in store when you enroll today.

What Cybersecurity Jobs Can I Pursue?
The cybersecurity field is an eclectic one. Jobs can be divided into two camps: blue team and red team. Let’s explore the differences and the job roles you can expect to encounter.
Blue Teams
Blue teams act as the defensive team, designing measures that protect systems and networks against potential threats.
- Security Operations Center (SOC) Analyst: A general awareness of all things cyber is a must with this role. As the “watchdog” for the organization, SOC analysts monitor networks for malicious activity, install security tools, help develop security strategies and stay up-to-date on cyber trends.
- Information Security Researcher: Information security research touches so many areas, including cyber forensics, social media and cryptography. This professional is in charge of ensuring that data is not compromised or accessed by unauthorized parties.
- NOC (Network Operations Center) Technician: This role maintains the IT equipment in an organization. This includes servers, networks and equipment. Their days usually consist of troubleshooting in the form of diagnosing, disclosing and solving the technical problems that can occur on a daily basis.
- Network Security Administrator: In collaboration with network engineers, these professionals ensure network-wide security with their ability to identify all network vulnerabilities, implement and configure security tools and build secure policies from the ground up.
- Digital Forensics Examiner: This professional works with crime investigations to recover digital data and analyze computers and electronic equipment to gather evidence for legal proceedings. They also assist organizations in the event of a security breach to determine how attackers gained access, what they did and if malware was implanted.
Red Teams
The red teams, on the other hand, act as the offensive team, leveraging ethical hacking procedures on their own systems to identify potential vulnerabilities.
- Penetration Tester: The function of this role is to simulate cyber attacks against your own system with the purpose of revealing any vulnerabilities. The concept is simple: find your weak points before malicious hackers do. Pen Testers use in-depth knowledge in one specific area to conduct their tests and is one of the features of ethical hacking.
- Offensive Cybersecurity Analyst: In order to understand which vulnerabilities need prioritizing, this professional uses threat analysis to assess weak points in the system and uncover policy violations. Collaboration with other red team professionals is necessary to share findings and minimize waste.
- Cybersecurity Crime Investigator: Similar to a Digital Forensics Examiner, this professional is focused primarily on digital crimes. The difference lies in their focus on internet-based crimes, analyzing systems and networks as opposed to files and data exclusively.
- Ethical Hacker: This role usually requires specific certifications, comprehensive knowledge of software programming and hardware, as well as excellent writing skills. Ethical hackers cover a range of hacking techniques to discover flaws in the system in addition to ensuring its security once the vulnerability has been found.
- Vulnerability Assessment Analyst: A strong attention to detail is required for this role as these professionals oversee the security of networks, operating systems and applications. They use manual testing techniques to familiarize themselves with the digital environment, perform vulnerability testing and conduct audits regularly.
Both blue and red teams are essential for closing any security gaps. As a cybersecurity professional, you will find that a role in any of these two camps rewarding and exciting.



How Much Do Entry-Level Cybersecurity Jobs Pay?
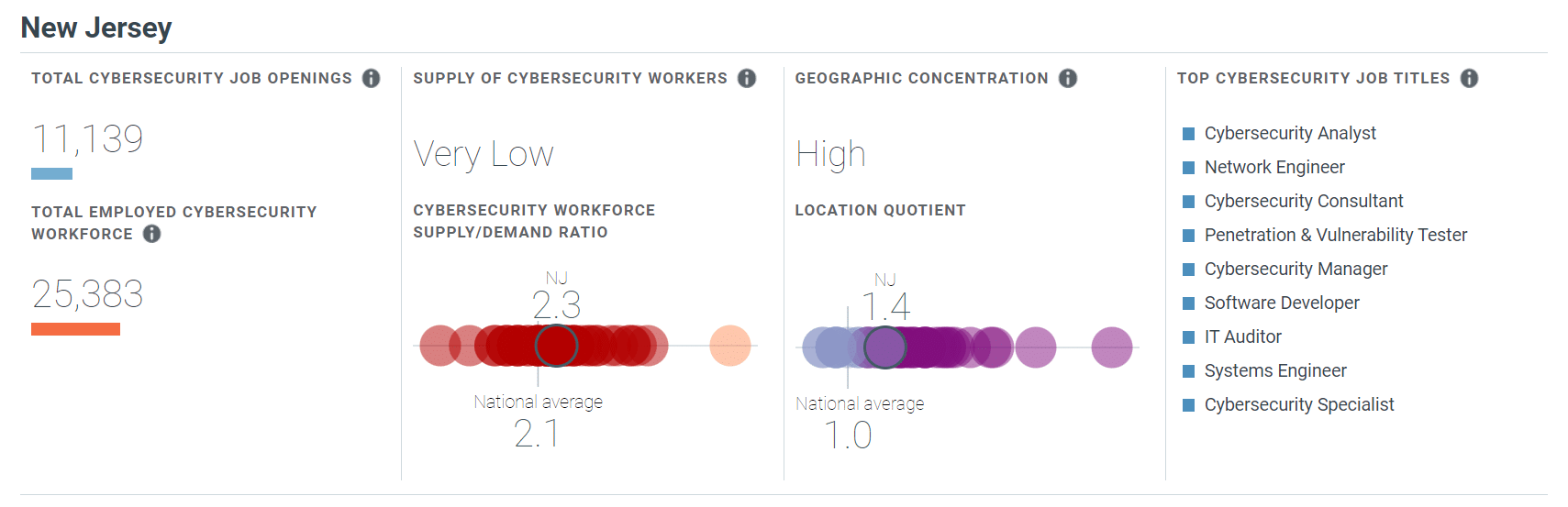
New Jersey is one of the top paying states for cybersecurity professionals, with an average annual salary of $121,600—well over the national average of $103,590. Of course, salaries will vary depending on levels of experience, the industry you work in and the organization you work with but entry-level cybersecurity professionals can expect to earn between $42,000 and $70,000 in New Jersey.
Major Industries for Cybersecurity Jobs
According to cyberseek.org, New Jersey has a large employment gap for cybersecurity professionals: there are currently over 11,000 job openings and a very low supply/demand ratio. In other words, if you’re looking for a career path with demand and a higher-than-average salary, a cybersecurity career path can provide opportunity and stability.
Financial services, advanced manufacturing, transport and logistics, healthcare and pharmaceuticals are the biggest industries in New Jersey and are each targets for cybercrime in their own way. Luckily, if neither of these industries interests you, you’ll be glad to know that cyber professionals are needed in every sector.
Begin Your Cybersecurity Career
By now, you’re fully aware of the potential for opportunity, growth and income within the cybersecurity field. Now it’s time to learn a bit more about our Cybersecurity Professional Bootcamp.
If you’re someone with no experience in the field or tech in general, you can still gain valuable training as it does not require previous experience. You will train from day one with real cybersecurity experts who know what’s expected of professionals in today’s workforce.
Victor Asalu, a learner in the NJIT Cybersecurity Professional Bootcamp, shares his experience:
Throughout the bootcamp, our team of student success managers will deliver additional resources and keep you accountable, while the career services team helps you build your professional brand and prepare you for the job hunt. The program is a part-time course with night and weekend classes over the span of 10 months, so you can pursue a new career without compromising your current job. At the end of the course, you will have a new set of technical skills, a completed professional portfolio to showcase to employers and a Cybersecurity Certificate from one of the top polytechnic universities.
Fill out the form below to get in touch with our admissions team to learn more.